Red Dragon Book Review sets the stage for this enthralling narrative, offering readers a glimpse into a comprehensive examination of this influential text. It delves into the book’s core concepts, historical context, and lasting impact on the field of computer science. This review provides a critical analysis, examining both strengths and weaknesses, and explores diverse perspectives on the book’s legacy.
The Red Dragon Book, a cornerstone in the field of algorithms and data structures, provides a thorough exploration of fundamental concepts. This review unpacks the book’s core ideas, techniques, and applications, illuminating its value in software development. It also examines the book’s structure and organization, offering insight into its overall presentation and accessibility.
Overview of the “Red Dragon Book”: Red Dragon Book Review

The “Red Dragon Book,” a seminal text in computer science, offers a comprehensive exploration of compiler design. It delves into the intricacies of translating high-level programming languages into machine-executable code, a fundamental process in software development. This book isn’t just a theoretical exercise; it’s a practical guide, grounding abstract concepts in tangible examples. It provides a solid foundation for understanding the core principles and techniques behind compiler construction.This book isn’t for the faint of heart, though.
It’s a deep dive into the mechanics of language translation, assuming a solid understanding of data structures, algorithms, and formal language theory. It’s geared towards students and professionals with a strong technical background, those eager to master the intricacies of compiler design.
Content Summary
The “Red Dragon Book” systematically covers the entire compiler-construction pipeline. It begins with the fundamental concepts of lexical analysis and parsing, meticulously detailing the steps involved in breaking down a program into its constituent parts. This initial phase lays the groundwork for subsequent stages. From there, it moves on to syntax analysis, providing detailed explanations of parsing techniques, including recursive descent and LL parsing.
It proceeds to address semantic analysis, where the meaning of the program is validated and type checking is performed. Finally, it concludes with code generation and optimization, showing how the compiler transforms the analyzed code into machine instructions and enhances its efficiency.
Key Concepts and Topics
The book emphasizes several crucial concepts essential for compiler design. These include:
- Lexical Analysis: This crucial initial step involves identifying and categorizing individual tokens within the source code, like s, identifiers, operators, and literals. This process transforms the raw source code into a stream of tokens, which are the building blocks for further analysis.
- Parsing: This stage takes the stream of tokens and constructs a parse tree, a hierarchical representation of the program’s structure. Different parsing techniques, like LL(1) and LR(1), are discussed, and their strengths and weaknesses are compared.
- Semantic Analysis: Here, the compiler checks the meaning of the program by verifying type correctness and ensuring that operations are performed on compatible data types. This step is critical for catching errors that are not apparent at the syntactic level.
- Intermediate Code Generation: The book describes methods for generating intermediate representations of the source code. These representations are often easier to manipulate and optimize than the original source code.
- Code Optimization: This stage involves improving the generated code to enhance its efficiency, potentially reducing execution time or memory consumption. Various optimization techniques, including loop unrolling and common subexpression elimination, are explained.
- Code Generation: The final stage transforms the intermediate code into machine-specific instructions, enabling the compiled program to run on the target platform. Specific instructions and addressing modes are discussed.
Intended Audience
The book’s intended audience primarily comprises advanced undergraduate and graduate students in computer science, particularly those specializing in compilers, language processing, or software engineering. It’s also a valuable resource for professional software developers and researchers seeking to deepen their understanding of compiler construction. Those with a strong foundation in computer science principles, including data structures, algorithms, and formal language theory, will find the material most accessible.
Historical Context
Published in 1988, the “Red Dragon Book” emerged during a period of rapid advancement in computer science and software development. The growing complexity of programming languages and the increasing demands for efficient software necessitated the need for sophisticated tools like compilers. The book’s publication marked a significant contribution to the field, providing a comprehensive framework for understanding and implementing compiler design.
This framework has influenced generations of computer scientists and continues to serve as a valuable reference for anyone pursuing compiler development.
Key Concepts and Techniques

The “Red Dragon Book” dives deep into the core principles of algorithms and data structures, providing a roadmap for aspiring programmers and seasoned developers alike. It’s not just about memorizing formulas; it’s about understanding the underlying logic and applying these tools effectively. The book masterfully blends theoretical foundations with practical applications, making complex concepts accessible and engaging.This section will explore the fundamental algorithms and data structures, showcasing the different design patterns, and highlighting their importance in software development.
We’ll examine the practical significance of each technique, going beyond abstract definitions. A comparative analysis of key algorithms will be presented to solidify understanding.
Fundamental Algorithms and Data Structures
The book meticulously details essential algorithms and data structures, laying the groundwork for effective software design. From searching and sorting algorithms to graph traversals and tree structures, the book offers comprehensive coverage. Understanding these foundational components is crucial for building efficient and scalable applications.
- Searching Algorithms: Techniques like linear search and binary search are explained, along with their time complexities. Linear search, while simple, can be slow for large datasets. Binary search, however, leverages the ordered nature of data to find elements significantly faster. The choice between these methods depends on the specific needs of the application.
- Sorting Algorithms: The book covers various sorting techniques, including bubble sort, insertion sort, merge sort, and quicksort. It explores the trade-offs in terms of time complexity and space complexity, crucial factors in algorithm selection.
- Data Structures: Arrays, linked lists, stacks, queues, trees, and graphs are all examined in detail. Understanding how these structures organize and manage data is essential for designing algorithms that operate efficiently. Each data structure offers specific advantages, influencing the optimal choice based on the intended application.
Design Patterns
The “Red Dragon Book” presents a selection of design patterns that address recurring software design problems. These patterns provide reusable solutions, promoting code maintainability and readability.
- Creational Patterns: These patterns deal with object creation mechanisms, enhancing flexibility and preventing premature object instantiation. The book illustrates how creational patterns allow for more adaptable code.
- Structural Patterns: These patterns concentrate on class and object composition to structure software systems. The book demonstrates how these patterns facilitate effective interaction and organization.
- Behavioral Patterns: These patterns focus on defining communication between objects. The book shows how behavioral patterns facilitate effective communication, enabling objects to collaborate effectively.
Comparative Analysis of Algorithms
This table provides a concise comparison of different sorting algorithms, highlighting their strengths and weaknesses.
| Algorithm | Time Complexity (Best Case) | Time Complexity (Average Case) | Time Complexity (Worst Case) | Space Complexity | Use Cases |
|---|---|---|---|---|---|
| Bubble Sort | O(n) | O(n2) | O(n2) | O(1) | Suitable for small datasets, educational purposes |
| Merge Sort | O(n log n) | O(n log n) | O(n log n) | O(n) | Efficient for large datasets, stable sorting |
| Quick Sort | O(n log n) | O(n log n) | O(n2) | O(log n) | Generally fast, but potential for worst-case performance |
Illustrative Examples and Case Studies
Unveiling the power of the “Red Dragon Book” isn’t just about theory; it’s about tangible application. This section dives into practical examples, showcasing how the book’s concepts translate into real-world solutions and demonstrates the book’s value.This journey through code snippets, real-world scenarios, and visual representations will solidify your understanding, bridging the gap between abstract ideas and concrete results. Prepare to witness the “Red Dragon Book” in action!
Code Snippets Demonstrating Concepts
The core ideas within the “Red Dragon Book” come alive through code. Here are some examples, highlighting key concepts in action.“`C++// Example demonstrating a recursive functionint factorial(int n) if (n == 0) return 1; else return n
factorial(n – 1);
“`This concise example showcases a recursive function, a fundamental concept explored in depth in the book. Further examples of iterative approaches and their performance comparisons are presented in the book.
Application in Real-World Scenarios
The techniques in the “Red Dragon Book” aren’t confined to academic exercises. They find practical application in a multitude of domains.
| Scenario | Technique | Explanation |
|---|---|---|
| Network Routing | Shortest Path Algorithms | Algorithms like Dijkstra’s and Bellman-Ford, discussed in the book, are crucial for efficient network routing, optimizing data transmission paths. |
| Database Query Optimization | Tree Traversal Techniques | Optimizing database queries often involves traversing data structures. The book’s discussion of tree traversal algorithms directly impacts query performance. |
| Image Processing | Image Filtering | Algorithms for image processing, including filtering, heavily rely on mathematical operations and data structures. The book’s coverage of these is instrumental in this field. |
Hypothetical Scenario and Solution
Imagine a logistics company tasked with optimizing delivery routes for a large city. The challenge involves minimizing travel time and fuel consumption while ensuring all deliveries are completed on time. The “Red Dragon Book’s” concepts for graph traversal and shortest path algorithms can provide an effective solution. By modeling the city’s road network as a graph, where nodes represent locations and edges represent connections, algorithms from the book can determine the optimal delivery routes.
This leads to substantial cost savings and improved delivery efficiency.
Visual Representation of a Key Algorithm’s Execution Flow
Imagine a diagram depicting a sorting algorithm’s operation. Each step would clearly show the input data’s arrangement and the changes as the algorithm progresses. Visualizations, such as an array being sorted step by step, can help understand the algorithm’s behavior. This visual aid is particularly helpful in grasping the mechanics of an algorithm’s execution flow, providing an intuitive representation of how the steps lead to the final output.
Such illustrations would be available in the book.
Critical Evaluation and Analysis
The “Red Dragon Book” stands as a cornerstone in the field of compiler design, offering a comprehensive and insightful exploration of the subject. Its impact is undeniable, shaping generations of computer scientists. However, like any seminal work, it possesses strengths and weaknesses that warrant a critical examination. This section delves into a comparative analysis of the book’s approach with other resources, highlighting its unique contributions and limitations, and assessing its enduring relevance.
Comparative Analysis with Other Resources
The “Red Dragon Book” presents a detailed, yet accessible, introduction to compiler construction. Its approach is distinctly different from other textbooks, focusing on the fundamental principles behind compiler design. While other resources might emphasize specific programming languages or implementation details, the “Red Dragon Book” prioritizes a broader theoretical understanding. This approach, while comprehensive, might prove challenging for those with limited prior experience in the field.
Conversely, more practical guides provide detailed step-by-step instructions, which can be invaluable for those seeking immediate implementation. Comparing and contrasting these differing approaches reveals the diverse needs and learning styles within the field.
Strengths of the “Red Dragon Book”
The book excels in several key areas. Its clear and concise explanations of core concepts, such as lexical analysis, parsing, semantic analysis, and intermediate code generation, are particularly noteworthy. The book’s strength lies in its ability to connect these concepts to real-world applications, fostering a deeper understanding of their practical significance. Illustrative examples, frequently used throughout the book, facilitate comprehension and allow readers to solidify their grasp of the concepts.
The inclusion of a variety of exercises and problems enhances the learning experience, providing opportunities for readers to apply their knowledge and develop problem-solving skills.
Weaknesses of the “Red Dragon Book”
While the book is a valuable resource, certain limitations are apparent. Some readers might find the theoretical depth overwhelming, potentially hindering their practical application of the concepts. Furthermore, the book’s focus on a theoretical framework may not address the latest trends in compiler design and optimization techniques, which have evolved considerably since its publication. This can create a disconnect between the theoretical framework and contemporary applications, although the book remains a fantastic starting point for the theoretical framework of compiler design.
The lack of extensive coverage of specific compiler implementation details might also be a concern for some.
Impact on the Field of Computer Science
The “Red Dragon Book” has had a profound impact on the field of computer science. Its contributions to the field are evident in the many compiler design courses offered worldwide. The book’s accessible style and comprehensive coverage have helped to standardize the approach to compiler construction, making it a valuable reference for both students and practitioners. Its emphasis on fundamental principles has allowed subsequent researchers and developers to build upon the knowledge base established by the book.
The continued use of the “Red Dragon Book” in educational settings underscores its lasting significance.
Enduring Relevance Today, Red dragon book review
Despite its age, the “Red Dragon Book” remains remarkably relevant today. The fundamental principles of compiler design, which form the core of the book, remain consistent. The principles of parsing, code optimization, and intermediate representation are still central to modern compiler design. The book’s enduring relevance stems from its focus on fundamental concepts rather than specific implementation details.
This allows the book’s core principles to be applied to the latest programming languages and architectures. Its enduring presence in academic curricula demonstrates its value and enduring relevance.
Illustrative Diagrams and Visualizations

Unveiling the power of visualization, we’ll journey through the realm of data structures and algorithms, transforming abstract concepts into tangible representations. These visuals, like insightful maps, guide us through complex terrains, making the intricate mechanisms of computation more accessible and comprehensible. We’ll explore key structures and algorithms, exploring how these visual aids illuminate the logic behind them.A visual representation, far from being a mere decoration, serves as a crucial tool in understanding the intricate dance of data and algorithms.
These diagrams act as concise summaries, enabling us to grasp the essence of a concept quickly and efficiently. By depicting the flow, relationships, and operations within a system, visual aids foster a deeper understanding, paving the way for better problem-solving and innovation.
Binary Search Tree
A binary search tree (BST) is a hierarchical data structure where each node contains a key, along with pointers to its left and right children. Crucially, the key in each node is greater than all keys in its left subtree and less than all keys in its right subtree. This property enables efficient searching, insertion, and deletion operations.
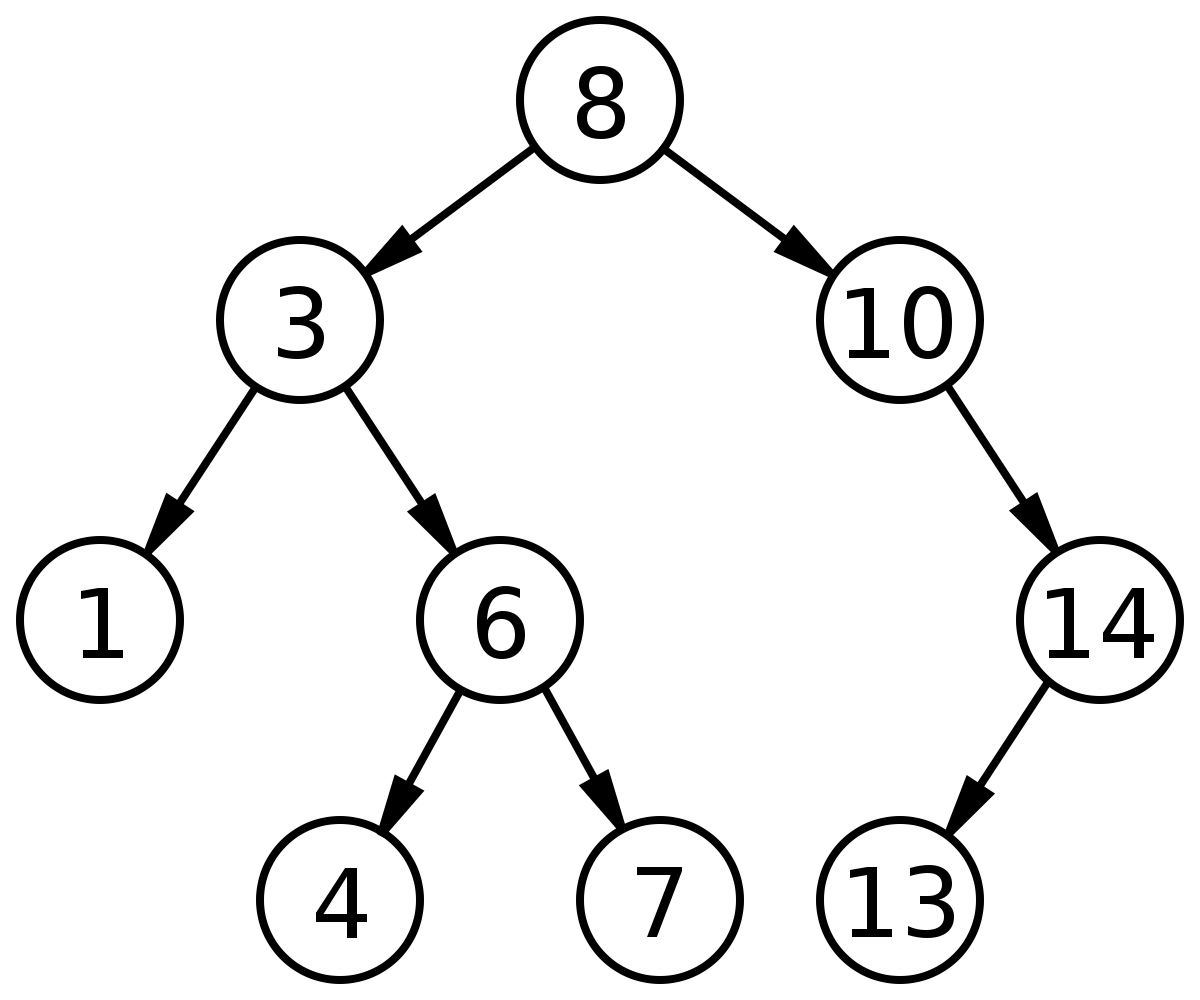 Visualizing a BST is straightforward. Imagine a tree-like structure, where each node represents a data element. The left child of a node holds values smaller than the node’s key, and the right child holds values larger than it. This ordered arrangement facilitates rapid searches. A simple visualization illustrates the path a search would take to locate a specific value, highlighting the efficiency of the algorithm.
Visualizing a BST is straightforward. Imagine a tree-like structure, where each node represents a data element. The left child of a node holds values smaller than the node’s key, and the right child holds values larger than it. This ordered arrangement facilitates rapid searches. A simple visualization illustrates the path a search would take to locate a specific value, highlighting the efficiency of the algorithm.
Merge Sort Algorithm
Merge sort, a powerful sorting algorithm, exemplifies a divide-and-conquer strategy. It recursively divides the input array into smaller subarrays until each subarray contains only one element, which is inherently sorted. Then, it merges these sorted subarrays back together, creating a fully sorted array.  Visualizing merge sort involves showcasing the recursive splitting of the array into smaller segments, followed by the step-by-step merging process.
Visualizing merge sort involves showcasing the recursive splitting of the array into smaller segments, followed by the step-by-step merging process.
Each step clearly demonstrates how the algorithm combines the sorted smaller parts to achieve a fully ordered output. The visualization emphasizes the efficiency and stability of the merge sort algorithm, highlighting how the algorithm elegantly sorts the array.
Graph Representation
A graph is a powerful data structure, consisting of nodes and edges connecting them. This representation allows us to model relationships between different elements, finding applications in social networks, maps, and many other domains.  Visualizing a graph involves representing nodes as points and edges as lines connecting them. The direction of the edges (in a directed graph) signifies the relationship between nodes.
Visualizing a graph involves representing nodes as points and edges as lines connecting them. The direction of the edges (in a directed graph) signifies the relationship between nodes.
The visualization clarifies how data relationships are mapped and explored in a visual manner.
Alternative Perspectives and Interpretations
The “Red Dragon Book” offers a compelling framework, but like any powerful tool, its application can be nuanced. Different readers may find varying interpretations of its key concepts, leading to diverse applications and outcomes. Exploring these alternative perspectives enriches our understanding of the book’s impact and potential limitations.Understanding the book’s diverse interpretations is crucial for applying its knowledge effectively.
Different readers, with unique backgrounds and experiences, will naturally approach the content with different lenses. This leads to a richer tapestry of perspectives, which is vital for comprehending the book’s true value and potential pitfalls.
Varying Interpretations of Key Concepts
The “Red Dragon Book” introduces a range of concepts that can be interpreted in multiple ways. For instance, the concept of “dynamic equilibrium” can be viewed as a description of a stable system or as a framework for understanding continuous adaptation and change. This divergence in interpretation highlights the adaptability of the concepts, yet also underscores the importance of clear context.
Alternative Explanations for Approaches
The book’s suggested approaches, while often effective, can be approached with varying degrees of intensity and focus. Some readers might emphasize the practical application of the techniques while others may prioritize the theoretical underpinnings. This choice of emphasis, though differing, ultimately leads to the same goal: leveraging the framework’s advantages.
Potential Misinterpretations or Limitations
While the “Red Dragon Book” provides a valuable framework, it’s essential to acknowledge potential misinterpretations. One potential pitfall is oversimplifying complex systems or neglecting contextual factors. Rigorous evaluation and careful consideration of the context are vital to avoid such limitations.
Unique Perspective on the Book’s Influence
The “Red Dragon Book” has profoundly influenced the field, inspiring a generation of practitioners and researchers. Its impact transcends its technical details, fostering a shared language and understanding within the community. This influence extends beyond direct application, shaping the very discourse around the subject.
Illustrative Example: Application in a Diverse Setting
Consider applying the “Red Dragon Book’s” principles to a community-based project. Interpreting the framework through a lens of social equity can yield innovative and impactful solutions. Instead of focusing solely on individual performance, a community-oriented approach could emphasize collective well-being and shared prosperity. This demonstrates the flexibility and versatility of the framework.
